Phishing attacks are evolving to become more sophisticated, as cybercriminals invest in new methods to deceive individuals into divulging sensitive information or installing malicious software. One of the recent trends in phishing involves the utilization of QR codes, CAPTCHAs, and steganography. These techniques are employed to carry out attacks and it is important to understand how they work in order to detect and prevent them effectively.
According to a video lesson on current trends in phishing attacks, one of the new trends involves phishing emails that resemble messages from a victim’s bank. This indicates that cybercriminals are increasingly using social engineering tactics to make their phishing attempts more convincing and difficult to detect. Additionally, the use of QR codes, CAPTCHAs, and steganography in phishing attacks highlights the adaptability of cybercriminals in exploiting new technologies to achieve their malicious objectives.
Furthermore, research suggests that phishing attacks are often carried out remotely, across networks such as the Internet. This underscores the need to study and understand Internet-borne malicious code in order to develop effective countermeasures against evolving phishing techniques. As technology continues to advance, it is crucial for individuals and organizations to stay informed about the latest trends in phishing attacks and to learn how to identify and protect against them.
Quishing
The rise of “Quishing,” a fusion of “QR” and “phishing,” has marked a significant trend among cybercriminals in the year 2023. This technique involves embedding malicious links within QR codes, providing a unique avenue for attackers to bypass conventional spam filters. Unlike text-based phishing attempts, where filters may be more effective, the use of QR codes introduces a layer of complexity that eludes the scrutiny of many security tools. Consequently, cybercriminals find Quishing to be an attractive and evasive method for orchestrating their attacks.
One notable advantage of Quishing lies in its ability to outsmart traditional security measures designed to analyze and block phishing attempts. Commonly employed filters that rely on text-based identification struggle to decipher the content concealed within QR codes, granting cybercriminals a strategic upper hand. This deficiency in security infrastructure enhances the appeal of Quishing as a preferred choice for those seeking to exploit vulnerabilities in online systems.
The core mechanism of Quishing involves the distribution of phishing attacks through emails containing QR codes with embedded malicious links. The QR code serves as a gateway to deceptive content, leading unsuspecting users to potentially harmful websites. In response to this emerging threat, security analysts and users alike are encouraged to adopt proactive measures for analyzing QR codes safely. Platforms such as ANY.RUN offer a solution, allowing users to scrutinize QR codes in a controlled environment.
To initiate the analysis process on ANY.RUN, users can follow a simple set of steps. By opening the task in the provided sandbox or uploading a file containing a QR code, individuals gain access to the Static Discovering section. Here, they can pinpoint the object housing the QR code and proceed to submit it for analysis. The sandbox then autonomously launches a new task window, facilitating the examination of the URL embedded within the QR code. This proactive approach empowers users to stay ahead of potential threats associated with Quishing attacks and enhances overall cybersecurity resilience.
A phishing campaign uses captchas to stall analysis
Hackers are increasingly using legitimate tools to make their campaigns appear more credible. But now, they’ve taken it a step further by using actual security solutions in their attacks.
The attack — which begins like a standard credential harvesting attempt and targets O365 credentials — uses a spam email as an initial vector. Hackers lure the user into logging into what appears to be legitimate software.
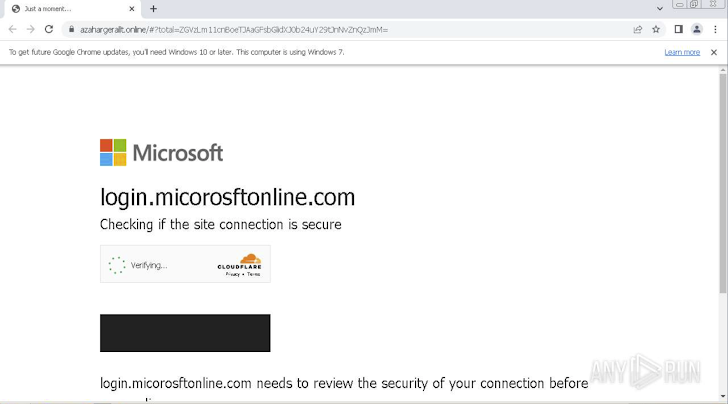
CAPTCHA, a widely employed security solution on websites, serves the primary purpose of thwarting automated bots aiming to create fraudulent accounts or submit spam. Despite its intended protective function, this tool has become susceptible to exploitation by attackers who have found ingenious ways to manipulate it to their advantage.
In recent instances, attackers have been leveraging CAPTCHAs as a cover for credential-harvesting forms embedded within deceptive websites. To achieve this, they employ a Randomized Domain Generated Algorithm (RDGA) to generate numerous domain names. By integrating CloudFlare’s CAPTCHAs into the process, they effectively obscure these forms from automated security systems, particularly web crawlers that lack the capability to circumvent the CAPTCHA challenge.
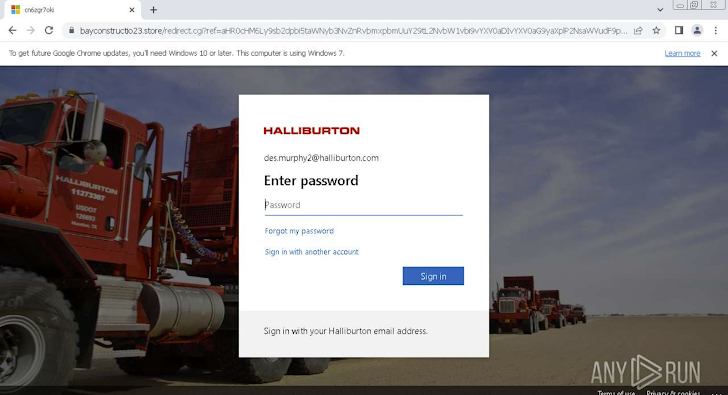
An illustrative case involves an attack directed at Halliburton Corporation employees. In this scenario, the assailants initiate the assault by subjecting the user to a CAPTCHA check, a seemingly innocuous step. Subsequently, they deploy a sophisticated tactic wherein a realistic Office 365 private login page, virtually indistinguishable from the authentic page, is presented.
The duplicitous nature of the attack becomes apparent as the victim, having successfully navigated the CAPTCHA challenge, enters their login credentials. Instead of landing on a malicious site, they are redirected to a legitimate website, a deceptive maneuver employed by the attackers to conceal their nefarious activities. Simultaneously, the pilfered credentials are surreptitiously transmitted to the attackers’ Command-and-Control server, completing the exploitation loop. This multifaceted approach underscores the evolving and intricate methods employed by cyber adversaries to compromise security measures meant to safeguard user information.
Steganography malware campaigns
Steganography, an age-old technique, involves the concealment of data within various types of media, such as images, videos, or other files. This covert practice is employed to hide information in plain sight, making it less likely to attract attention.
In the context of a phishing attack, steganography unfolds as a sophisticated strategy. The attack typically initiates with a meticulously crafted email designed to mimic legitimacy. Disguised within this email is an attachment, often in the form of a Word document, accompanied by a link leading to a file-sharing platform like Dropbox. A concrete illustration is provided in the case of a fraudulent email purporting to be from a Colombian government organization.
Upon interaction with the document by an unsuspecting recipient who clicks the embedded link, an archive is downloaded. This archive harbors a VBS script file. Upon execution of this script, it retrieves an image file that outwardly appears innocuous but is, in fact, concealing malicious code within its depths. The unsuspecting victim, in executing this seemingly harmless image file, unwittingly triggers the activation of malware, thereby compromising the security of their system. This method illustrates the increasingly sophisticated and duplicitous techniques employed by cybercriminals in their persistent efforts to infiltrate systems and compromise user data.
Sources :
https://thehackernews.com/2023/11/how-multi-stage-phishing-attacks.html
https://any.run/cybersecurity-blog/new-phishing-tactics/?utm_source=thehackernews&utm_medium=article&utm_campaign=multistagephishing&utm_content=blog&utm_term=211123
https://any.run/cybersecurity-blog/steganography-in-malware-attacks/?utm_source=thehackernews&utm_medium=article&utm_campaign=multistagephishing&utm_content=blog&utm_term=211123
https://quizlet.com/536985618/cs-1000-cc3e-ch07-topic-74-video-lesson-what-are-current-trends-in-phishing-attacks-flash-cards/
https://theses.cz/id/6pfteu/Kryptoanaly_za/bin/LangStats/english/topwords.txt
https://www.sweetstudy.com/files/charlesp-pfleegersharilawrencepfleegerjonathanmargulies-securityincomputing-prenticehall2015-pdf-8560507
https://www.cs.auckland.ac.nz/~pgut001/pubs/book
https://www.researchgate.net/publication/362347620_IoT-Enabled_5G_Networks_for_Secure_Communication