Cloud computing is an advancement in information technology as a method of delivering various services over the internet and remotely in the “cloud” or virtual space. With this technology, the use of physical devices is reduced because all processes and data storage are carried out through virtual space so that it can be done anytime and anywhere as long as there is internet access. In this rapidly growing technology, data security is an interesting and important topic for researchers.
The paper written by Ullah et al. with the title “Cloud and internet-of-things secure integration along with security concerns” published in the International Journal of Informatics and Communication Technology (IJ-ICT) Volume 12, Issue 1, April 2023 discusses the integration of cloud computing and internet of things (IoT) and the security issues that arise from the integration.
The authors provide an overview of both technologies and highlight the security challenges that should be addressed to ensure secure integration. The paper concludes by discussing the importance of addressing these security issues to enable the full potential of cloud computing and IoT to be realized [1].
Types of cloud computing attacks
It is without a doubt that the convenience and cheapness of cloud computing services have changed our daily lives. However, the security issues associated with cloud computing make us vulnerable to cyber crimes that occur every day. Attacks can cause damage to cloud infrastructure (devices), access, and cloud computing networks.
1. VM rollback attack
This attack is carried out by tricking the target into running an older, less secure software version. This attack forcibly targets cloud infrastructure. This attack results in damage to the cloud infrastructure and data leakage.
2. Denial of service (DoS) attack
Denial of service (DoS) is a type of cyberattack to prevent legitimate users from accessing by flooding the traffic of a system, network, or device by sending information that triggers damage.
3. Thief-of-service attack
This attack allows attackers to obtain paid credentials for free.
4. Cross VM side Chanel attack
This attack leverages hardware when two virtual machines (VMs) share physical resources, such as CPU cache. This allows an attacker to obtain access to sensitive information from one VM by monitoring the behaviour of the other VM.
5. Botnets attack
A botnet attack is a cyber attack that uses a network of infected devices, known as bots, to perform malicious tasks.
6. Phishing
Phishing is a social engineering attack that attempts to trick victims into revealing personal information, such as passwords, credit card numbers, or social security numbers. Phishing attacks are often carried out through email, but can also be carried out through text messages, social media, or even phone calls.
7. Cloud malware injection
A type of attack that involves injecting malicious code into a cloud environment. The attacker inserts code so that the system malfunctions.
The domain of security attacks on different hybrid devices is increasing day by day. Recently IoT was adopted the most in terms of connection of new devices over the internet. Every day these smart devices are targeted by attackers, they try different methods to get the desired goal [3].
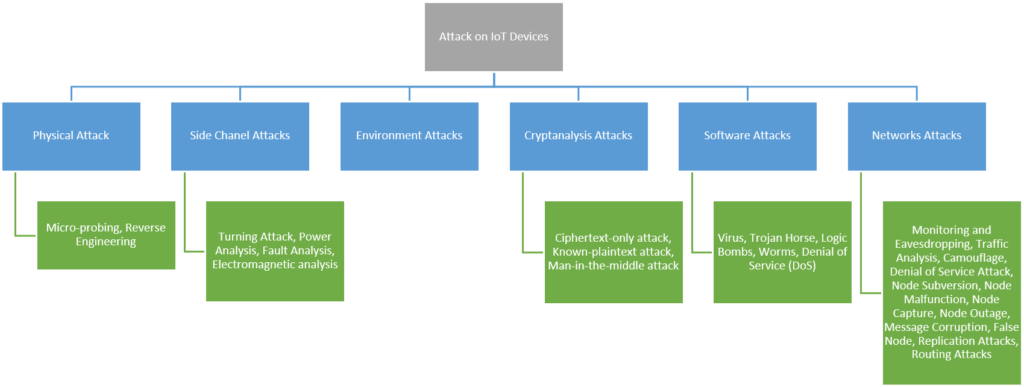
Security challenges in IoT and cloud computing
1. Data security:
The integration of IoT with cloud computing poses security challenges for stored data. Cloud computing provides highly scalable and flexible storage, but also introduces new security risks to data stored in the cloud [4].
2. API gateway misconfiguration
IoT relies on cloud computing to integrate servers, analyze information collected from sensors, increase processing power, and increase storage capacity. The main cloud-related challenges facing IoT include API gateway misconfiguration, which can lead to unauthorized access to data [5].
3. Identity and access management (IAM) misconfiguration
Successful data breaches still occur due to weak credentials. Since passwords are still the primary means of authentication, companies should implement strict password policies to prevent abuses. IAM misconfiguration can also lead to unauthorized access to data [5].
4. Heterogeneity
The heterogeneity of devices in IoT networks poses challenges to security. Different devices have different security requirements, and it may be hard to ensure that all devices are secure [6].
5. Performance
Integrating IoT with cloud computing can pose problems with latency, bandwidth requirements, and reliability [7].
6. Firmware and software vulnerabilities
Ensuring the security of IoT systems is complex, mainly because many smart devices have limited resources. Attackers easily exploit vulnerable firmware and software to gain unauthorized access to devices and data [8].
Tips for securing IoT devices and cloud computing services
The integration of IoT with cloud computing poses several security challenges that need to be addressed to ensure secure integration. These challenges include data security, API gateway misconfiguration, IAM misconfiguration, heterogeneity, performance, and firmware and software vulnerabilities. Securing connected IoT devices and cloud services is essential to prevent data leakage and unauthorized access to sensitive information. Here are some best practices for securing IoT devices and connected cloud computing services:
- Use secure passwords: use strong passwords for connected IoT devices and cloud services. Weak passwords are still the primary means of authentication, and implementing a strict password policy can prevent breaches [5].
- Security design: design security into IoT devices and connected cloud services from the beginning. Consider the security at every stage of the development process, from design to deployment [9].
- Update firmware and software: regularly update the firmware and software of IoT devices to prevent vulnerabilities from being exploited by attackers [8].
- Monitor devices and networks: monitor IoT devices and networks for unusual activity that could indicate a security breach. Review logs and audit trails regularly to detect potential security incidents [6].
- Using encryption: Use encryption to protect data in transit and at rest. Encryption can help prevent unauthorized access to sensitive information [1].
- Restrict access: Limit access to connected IoT devices and cloud services to only those who need them. Use role-based access control to ensure that the users only have access to the data and services they need to do their jobs [9].
Securing connected IoT devices and cloud services is critical to preventing data breaches and unauthorized access to sensitive information. Best practices for securing IoT devices and linked cloud services include using secure passwords, designing out security, updating firmware and software, monitoring devices and networks, using encryption, and restricting access.
References:
- Cloud and internet-of-things secure integration along with security concerns | Ullah | International Journal of Informatics and Communication Technology (IJ-ICT)
- Design and Build Disaster Emergency Response Systems Using Firebase Cloud Messaging Based on Android and SMS Gateway | Prasetyo | Jurnal Informatika
- Keynote Paper: From EDA to IoT eHealth: Promises, Challenges, and Solutions | Firouzi | IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems
- Security Challenges and Strategies for the IoT in Cloud Computing | Mohiuddin | 2020 11th International Conference on Information and Communication Systems (ICICS)
- Addressing Cloud-Related Threats to the IoT | trendmicro
- Discovering and Understanding the Security Issues in IoT Cloud | Almolhis | International Journal of Computer Science and Security (IJCSS)
- Performance and Security Issues of Integrating Cloud computing with IoT | Walia | Emergent Converging Technologies and Biomedical Systems
- Internet of Things (IoT) Security: Challenges and Best Practices | apriorit
- Careful Connections: Keeping the Internet of Things Secure | Federal Trade Commission
by: Dwi Ilham and Septian D. Cahyo

