Security experts have discovered that a significant number of IT administrators are employing tens of thousands of easily guessable passwords to safeguard their portal access, which exposes enterprise networks to potential cyberattacks. Among the over 1.8 million administrator credentials examined, more than 40,000 of them were simply “admin,” indicating a widespread preference for the default password among IT administrators.
Default and weak passwords
Passwords that are either set to their default values or are not very strong in terms of security were the focus. This authentication information was gathered from January to September of the current year, using Threat Compass, a threat intelligence tool provided by the cybersecurity firm Outpost24.
Outpost24 reports that the authentication credentials were sourced from malicious software designed to steal information, typically targeting applications that store both usernames and passwords. Although the acquired data was not presented in plain text, the researchers assert that “most of the passwords in our inventory could have been easily guessed in a relatively simple password-guessing attack.”
To narrow down their list of passwords specific to administrators, they combed through the statistical information stored in the Threat Compass backend, identifying pages categorized as Admin portals. In total, they unearthed 1.8 million passwords that were recovered between January and September of 2023.
An admin portal, depending on its purpose, can grant access to configuration settings, user accounts, and security configurations. Additionally, it might enable functions like customer and order tracking or support create, read, update, delete (CRUD) operations for databases.
Subsequent to their analysis of the authentication credentials related to admin portals, Outpost24 compiled a ranking of the 20 weakest sets of authentication credentials.
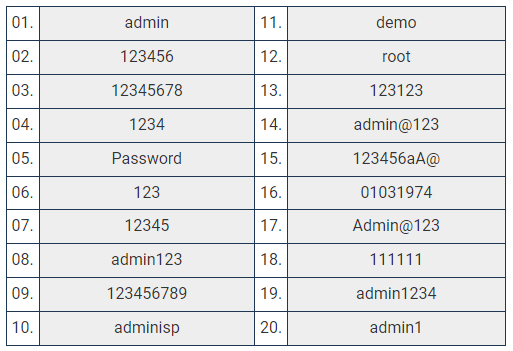
The researchers caution that while the listed passwords are somewhat common and foreseeable, they are linked to admin portals, and malicious actors are actively pursuing privileged user accounts.
Safeguarding the enterprise network should begin by adhering to fundamental security guidelines, such as employing lengthy, robust, and distinct passwords for each account, particularly for those with access to sensitive assets.
To mitigate the risks associated with data-stealing malware, Outpost24 suggests implementing an endpoint and detection response system, deactivating features that save and auto-fill passwords in web browsers, verifying domains during redirections, and refraining from using cracked or pirated software.

