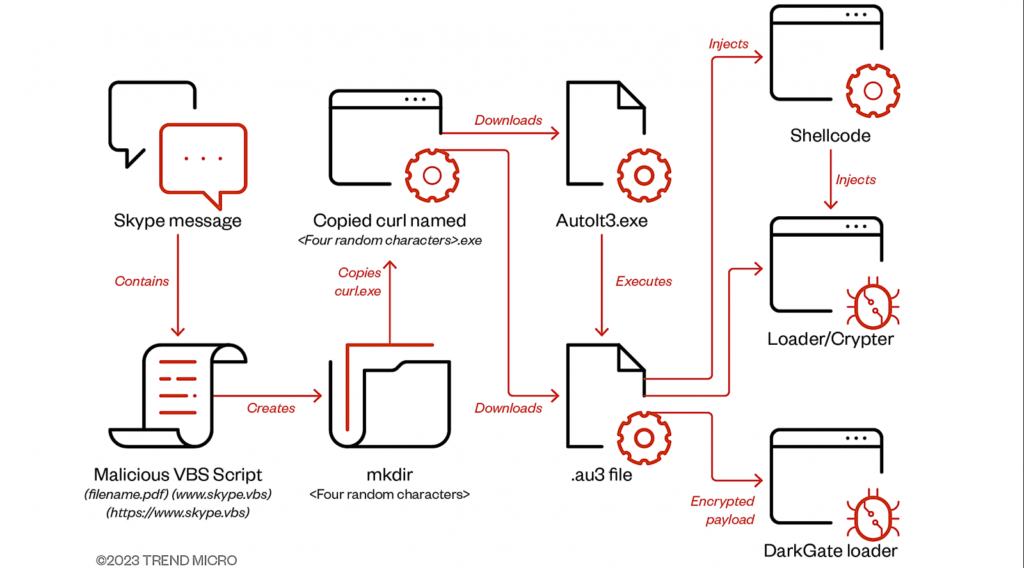
Between July and September, DarkGate malware assaults have leveraged hacked Skype accounts to contaminate intended victims via messages containing VBA loader script attachments. According to Trend Micro security researchers, who identified these attacks, this script is responsible for fetching a second-stage AutoIT script, which is tailored to deposit and run the final DarkGate malware payload.
Trend Micro noted that the attacker’s access to the victim’s Skype account allowed them to hijack an ongoing messaging thread and customize the file names to align with the chat history context. The method by which the instant messaging application accounts were initially compromised remains uncertain, but it is suggested to be either through leaked credentials available on underground forums or as a result of the parent organization’s prior security breach.
In addition, Trend Micro observed DarkGate operators attempting to disseminate their malware payload through Microsoft Teams within organizations that had configured the service to accept messages from external users. Prior instances of Teams phishing campaigns using malicious VBScript to deploy the DarkGate malware had also been identified by Truesec and MalwareBytes.
According to their explanation, malicious actors directed their efforts towards Microsoft Teams users by exploiting compromised Office 365 accounts originating from entities outside their organizations. They also utilized a publicly available tool called TeamsPhisher. This tool afforded attackers the ability to circumvent restrictions on incoming files from external tenants and send phishing attachments to users of Microsoft Teams.
Their ultimate objective remains consistent: infiltrating the entire environment. Depending on the specific threat group that obtained or leased the particular DarkGate variant in use, the nature of the threats may vary, encompassing anything from ransomware to cryptomining. Trend Micro indicated, “From our telemetry, we have observed that DarkGate is frequently linked to the tools commonly used by the Black Basta ransomware group.”
The DarkGate malware loader has seen a notable increase in its adoption by cybercriminals as a means of gaining initial access to corporate networks. This trend emerged following the disruption of the Qakbot botnet in August, which was a result of international collaborative efforts.
Prior to the dismantling of Qakbot, an individual claiming to be the developer behind DarkGate sought to market subscriptions on a hacking forum, proposing an annual cost of up to $100,000 for the service. The malware, as described, was promoted for its extensive range of features. These included a hidden VNC (Virtual Network Computing), the ability to bypass Windows Defender, a tool for pilfering browser histories, an integrated reverse proxy, a file manager, and a Discord token-stealing capability.
Following this announcement, there has been a noticeable increase in reported instances of DarkGate infections using a variety of delivery methods, such as phishing and malvertising. This recent surge in DarkGate activity serves to underscore the escalating influence of this malware-as-a-service (MaaS) operation within the realm of cybercrime. It also highlights the unwavering determination of threat actors to persist in their attacks, adapting their tactics and methods in response to disruptions and challenges.

