Threat actors are exploiting the ‘Citrix Bleed’ vulnerability, identified as CVE-2023-4966, to focus on governmental, technological, and legal institutions across regions such as the Americas, Europe, Africa, and the Asia-Pacific area.
According to findings from Mandiant researchers, there are four continuous campaigns aimed at susceptible Citrix NetScaler ADC and Gateway devices, with these attacks having been initiated since late August 2023.
The security firm has observed post-exploitation actions linked to stealing credentials and moving laterally, emphasizing that this form of exploitation doesn’t leave much forensic evidence, rendering these attacks notably elusive.
Citrix Bleed
Thousands of Citrix NetScaler ADC and Gateway instances remain unpatched against a critical vulnerability that is being widely exploited, security researchers warn. The vulnerability, known as CVE-2023-4966 or Citrix Bleed, allows unauthenticated attackers to leak sensitive information from on-prem appliances that are configured as an AAA virtual server or a gateway. Citrix released patches for the bug on October 10 and warned last week that threat actors are actively exploiting the vulnerability in the wild to perform session hijacking, which allows them to completely bypass authentication, including multi-factor authentication protections.
The NetScaler suite of products includes load balancing, firewall, and VPN services, so one possible impact is compromised remote access to private networks. NetScaler responds to certain requests by dumping memory back to the sender, which can contain access tokens for logged-in users. The exploit is as bad as whatever you’ve given access to remotely through your NetScaler system. And because they’re logged-in sessions, MFA won’t protect you. It’s not yet clear which user sessions are typically included in the memory dump from the information available on the exploit, although the public exploit doesn’t provide a way for an attacker to control which sessions are attacked. This may limit the impact, but since Citrix has rated the weakness as a CVSS 9.4, it’s better to err on the side of caution and assume it could include highly privileged accounts.
Over the past few days, security researchers have started raising the alarm on CVE-2023-4966 being widely exploited, with multiple threat actors, including ransomware groups, targeting internet-accessible NetScaler ADC and Gateway instances. The ongoing mass exploitation started around the same time Assetnote published a technical writeup of the vulnerability and a proof-of-concept (PoC) exploit for it. According to security researcher Kevin Beaumont, however, the mass exploitation has not necessarily been triggered by the PoC publication, as “it was clear multiple groups had already obtained technical details”.
By exploiting the vulnerability, attackers gain memory access to NetScaler ADC and Gateway appliances, which allows them to extract session cookies and attempt to bypass authentication. This means that even patched instances are at risk of exploitation, as the session tokens persist in memory. The vulnerability is severe because it can bypass multi-factor authentication protections, and the impact depends on which user sessions get exposed and what permissions the affected user has.
The vulnerability is severe because it can bypass multi-factor authentication protections, and the impact depends on which user sessions get exposed and what permissions the affected user has. While CISA and Mandiant identified zero-day exploitation of this vulnerability in August, researchers at AssetNote looked into the vulnerability and have now developed a reliable exploit. The exploit is reminiscent of hacking in 1999 – send 24,812 “a” characters to the target system and receive a user session in reply.
Citrix claims to have more than 400,000 customers worldwide, including 99% of Fortune 100 companies and 98% of Fortune 500 companies, from Microsoft and CNET to eBay. In a blog post, Mandiant suggests victims so far include tech companies, government organizations, and professional services companies. Citrix has released a patch for the flaw, which users should apply immediately, and recommends killing all active and persistent sessions to fully address the issue, as compromised sessions can persist through a patch. Multiple threat actors, including ransomware groups, are exploiting the vulnerability, targeting internet-accessible NetScaler ADC and Gateway instances. Mandiant has seen attacks targeting government, legal and professional services, and technology organizations in the Americas, EMEA, and the APAC regions. Organizations should apply the available patches and then kill all active and persistent sessions to fully address the issue, as compromised sessions can persist through a patch.
Ongoing attacks
Mandiant has pointed out that the absence of comprehensive logging on these appliances makes it difficult to investigate the exploitation of CVE-2023-3966. To address this challenge, it is necessary to utilize web application firewalls (WAF) and other network traffic monitoring tools to log traffic and determine whether a device has been compromised. This means that without this type of monitoring in place prior to an attack, historical analysis is not feasible, and researchers are confined to real-time observations.
Furthermore, even after an attack, the threat actors remain covert by using techniques that blend in with everyday operations, such as employing common administrative tools like net.exe and netscan.exe. Mandiant has managed to identify exploitation attempts and session hijacking by focusing on several key pathways:
- WAF request analysis: WAF tools can log requests made to the vulnerable endpoint, providing a valuable source of information.
- Login patterns monitoring: Monitoring for inconsistencies in client and source IP addresses, as well as detecting multiple sessions from the same IP address recorded in ns.log files, can indicate potential unauthorized access.
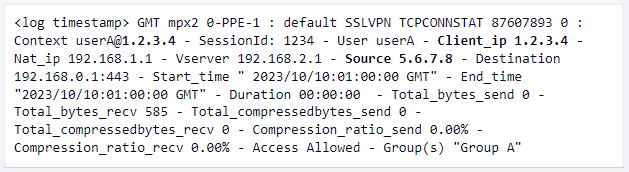
- Windows Registry correlation: By cross-referencing Windows Registry entries on Citrix VDA systems with ns.log data, it becomes possible to trace the origin of the attacker.
- Memory dump inspection: Analyzing NSPPE process memory core dump files for unusual strings with repetitive characters can help identify exploitation attempts.
Objectives of the Attack
Following the exploitation of CVE-2023-4966, the attackers proceed with network reconnaissance, which involves the theft of account credentials and lateral movement through Remote Desktop Protocol (RDP).
During this phase, the threat actors employ various tools, including:
- net.exe – Used for Active Directory (AD) reconnaissance.
- netscan.exe – Utilized for internal network enumeration.
- 7-zip – Employed to create encrypted segmented archives for compressing reconnaissance data.
- certutil – Used to encode (base64) and decode data files and deploy backdoors.
- e.exe and d.dll – Loaded into the LSASS process memory to create memory dump files.
- sh3.exe – Executes the Mimikatz LSADUMP command for credential extraction.
- FREEFIRE – A novel lightweight .NET backdoor that uses Slack for command and control.
- Atera – Utilized for remote monitoring and management.
- AnyDesk – Employed for remote desktop access.
- SplashTop – Utilized for remote desktop access.
While many of these tools are commonly found in enterprise environments, their combined deployment may indicate a compromise, and the presence of tools like FREEFIRE is a clear sign of a breach. The researchers have also released a Yara rule that can be used to detect the presence of FREEFIRE on a device.
Mandiant notes that the four threat actors exploiting CVE-2023-4966 in different campaigns exhibit some overlap in the post-exploitation stage. All four extensively use tools such as csvde.exe, certutil.exe, local.exe, and nbtscan.exe, and two activity clusters were observed using Mimikatz. It’s important to note that applying available security updates does not address existing breaches, necessitating a comprehensive incident response.
Sources :
https://www.bleepingcomputer.com/news/security/hackers-use-citrix-bleed-flaw-in-attacks-on-govt-networks-worldwide/
https://www.mandiant.com/resources/blog/session-hijacking-citrix-cve-2023-4966
https://www.tenable.com/blog/cve-2023-4966-citrix-netscaler-adc-and-netscaler-gateway-information-disclosure-exploited-in
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-289a
https://www.securityweek.com/mass-exploitation-of-citrix-bleed-vulnerability-underway/
https://www.rapid7.com/blog/post/2023/10/25/etr-cve-2023-4966-exploitation-of-citrix-netscaler-information-disclosure-vulnerability/
https://www.esecurityplanet.com/trends/weekly-vulnerability-recap-october-30-2023/
https://www.intruder.io/blog/how-bad-is-the-citrixbleed-vulnerability-cve-2023-4966
https://arstechnica.com/security/2023/10/critical-citrix-bleed-vulnerability-allowing-mfa-bypass-comes-under-mass-exploitation/
https://www.malwarebytes.com/blog/news/2023/07/citrix-netscaler-vulnerability-added-to-known-to-be-exploited-catalog/amp

