A figure known as Prolific Puma, identified by security experts, has been offering cybercriminals the service of shortening links for over four years without attracting attention due to their discreet operations.
Within just a month, Prolific Puma has managed to create numerous domains, including many within the U.S. top-level domain (usTLD), to facilitate the distribution of phishing schemes, fraudulent activities, and malicious software.
Short URL service for cybercriminals
Recent research reveals that the .US top-level domain hosts a substantial number of domains associated with a malicious link-shortening service called ‘Prolific Puma,’ which actively promotes malware and phishing schemes. Over the past three years, security firm Infoblox has been monitoring this service, which employs short domains from uncooperative providers to conceal harmful landing pages.
In just a month, this actor has registered a multitude of domains, primarily within the U.S. top-level domain (usTLD), facilitating the distribution of phishing, scams, and malicious software.
Approximately six months ago, Infoblox first detected Prolific Puma’s activities when they noticed a domain generation algorithm being used for this malicious URL shortening service. Nevertheless, they could track the short links but often couldn’t trace the final landing page.
The inconsistencies observed in the short links suggest that multiple cybercriminals may be using Prolific Puma’s services, with text messages being a primary method of delivery.
Prolific Puma has registered around 75,000 unique domain names since April 2022, with a significant surge in short domain registrations earlier in the year, with most being in the usTLD.
Despite policy restrictions, almost 2,000 domains associated with Prolific Puma’s activities have been privately registered within the usTLD.
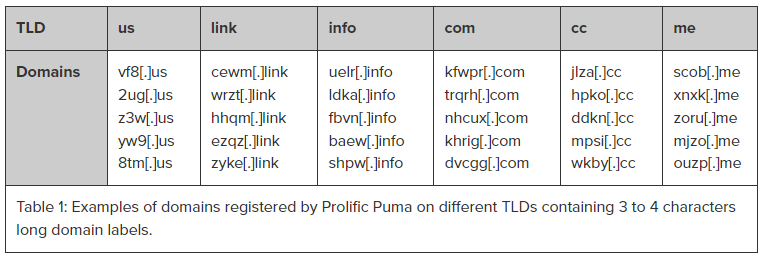
Typically, these domains are alphanumeric and vary in length, with the most common consisting of three to four characters. To avoid detection, Prolific Puma delays the activation of these domains.
Over the past three years, the primary hosting service used has been NameSilo, a domain registrar commonly favored by cybercriminals. Once activated, these domains are transferred to bulletproof hosting providers.
While it seems that Prolific Puma only offers the short link service, there is no confirmation regarding whether they control the landing pages.
Despite not actively advertising on underground markets, Prolific Puma’s extensive and dynamic operations, spread across various registrars, have enabled it to remain largely under the radar.
Massive operation
Detection and Domain Name Characteristics
To enhance the capabilities of our Infoblox DNS detection and response products, both in the cloud and on-premises, Infoblox have developed a comprehensive set of independent algorithms. These algorithms are designed to identify suspicious and malicious domains, along with associated IP addresses and other DNS resources. By collecting passive DNS (pDNS) query logs and utilizing other data sources, Infoblox perform a series of analyses on newly queried, registered, or configured domains. These analyses independently profile these domains, ranging from flagging them as suspicious to attributing them to a DNS threat actor.
The discovery of Prolific Puma followed a typical path taken by many of the DNS threat actors Infoblox internally identify and track. Initially, some related domains were individually flagged as suspicious through our automated analytics. While this helped block these domains in our DNS recursive resolvers to safeguard our customers, it didn’t necessarily provide a comprehensive view of the actor’s activities or correlate these domains to a single actor. In the spring of 2023, when Infoblox introduced algorithms for RDGA (Registered Domain Generation Algorithm) discovery, Infoblox began identifying Prolific Puma domains in clusters. These clusters were also automatically determined but utilized statistical methods to ensure a high level of confidence that the RDGA domains were registered by the same DNS threat actor. Subsequently, another algorithm detected unusual behavior in IP resolutions and linked the individual RDGA clusters.
Since April 2022, they have registered between 35,000 and 75,000 unique domain names. Picture below illustrates the daily registration of unique domain names using three or four long domain labels. As Infoblox have recently reported, RDGAs have increasingly replaced traditional DGAs (Domain Generation Algorithms), posing new challenges for defenders. This technique allows Prolific Puma to automate their operations for scalability. Infoblox detects thousands of new domains daily that are generated by an RDGA, and Prolific Puma is among them.
Prolific Puma utilizes NameSilo as their domain name registrar and typically applies a strategic aging process to their domains before hosting their service with anonymous providers. Despite having no apparent connection to the United States, Prolific Puma consistently exploits the us top-level domain (usTLD), which is intended to be reserved for U.S. citizens and organizations. Prolific Puma is known to register both new domains and domains that have been dropped. As an example, the domain 3ty[.]us was previously used by a different actor for Facebook messenger phishing campaigns in June 2022 and was subsequently registered by Prolific Puma after it became available in July 2023.
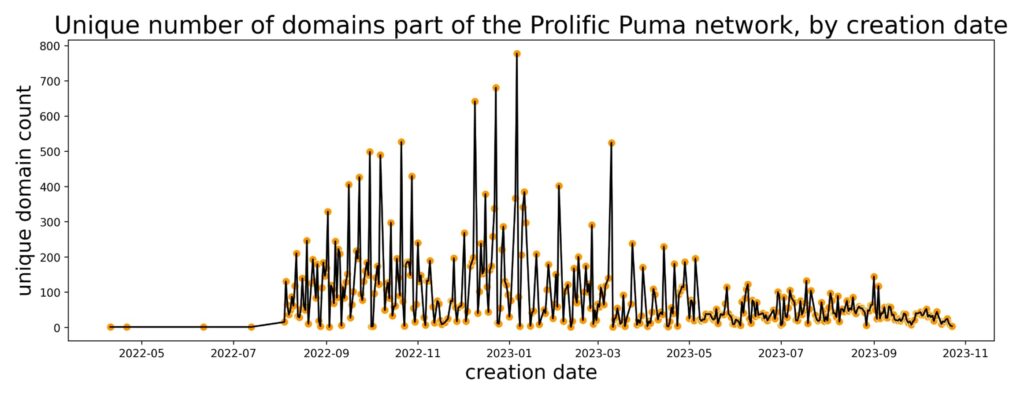
Prolific Puma domains are spread across 13 TLDs. Since May this year, though, the actor used the usTLD for more than half of the total domains created, the daily average being 43.
Since mid-October, the researchers noticed closed to 2,000 domains in the usTLD indicating Prolific Puma activity that are behind private registration protection.
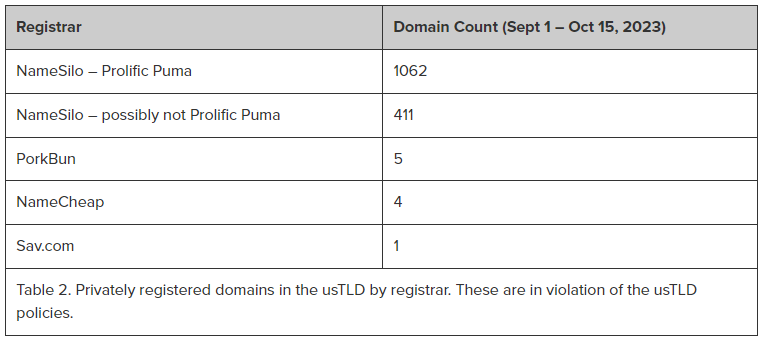
It’s important to note that, according to the current policy, private registrations are not allowed within the .US domain, and registrants are mandated to furnish accurate and genuine information.
Additionally, registrars are obligated not to provide private domain registration services to those who register .US domain names.
Prolific Puma domains typically exhibit alphanumeric and pseudo-random characteristics, with variations in size, although three or four-character domains are the most frequently encountered. Nevertheless, the research team did identify domains that extended to seven characters in length.
Over the past three years, the actor predominantly utilized hosting services from NameSilo, an inexpensive internet domain registrar known for being frequently exploited by cybercriminals. NameSilo offers an API for bulk domain registration.
To evade scrutiny and detection, Prolific Puma employs a strategy of aging its domains by leaving them inactive or parked for several weeks. During this period, the actor initiates a limited number of DNS queries to establish a reputation.
Once ready for active use, the actor transfers these domains to a bulletproof hosting provider, paying in Bitcoin cryptocurrency to secure a virtual private server with a dedicated IP address.
Infoblox observed that some of these domains are eventually abandoned, but the DNS records continue to point to the dedicated IP.
The researchers speculate that Prolific Puma likely only provides the short link service and does not control the landing pages. However, they do not rule out the possibility that the same actor may oversee the entire operation.
An Example Campaign
Prolific Puma operates a link shortener for a variety of phishing, scam, and malware activities. Below is describe an example of one of the campaigns it serves. The link leads to a phishing page designed to appear like an email, prompting the user to provide personal details and make a payment, and then it infects the user with browser plug-in malware.
The technical steps between the shortened link and the browser plug-in malware in this campaign are as follows:
- The first short link http://bwkd[.]me/ZFjfA3 redirects to http://ksaguna[.]com/click.php?key=, which itself redirects to the address https://www[.]asdboloa[. ]com/ZA/AB_zagopb/?uclick=
- This last website is a fake Gmail message that tells users that they have won the opportunity to test the new iPhone 15.
- The user is instructed to click on a link to claim their phone at https://www[.]game[.]co[.]za/2023program and enter their delivery information. The website www[.]game[.]co[.]za is a South African discount retailer using promotional drives to draw consumers.
- Following this link under the right conditions leads to a prompt to pay 18 South African Rand (ZAR) to participate in the trial.
- From there, the user is presented with a page claiming to be postal tracking and prompting them to accept notifications from fubsdgd[.]com. Clicking “accept” triggers the installation of browser malware that uses the OneSignal service to push notifications. While commonly associated with ads, in our experience, browser plug-in malware is commonly used to deliver scams, phishing, and other malware, along with ads.
- Finally, the victim is taken through a series of prompts asking them to verify shipping preferences and enter their personal information.
As per Infoblox’s findings, the actor refrains from promoting its link shortening service in underground markets, yet it remains the largest and most dynamically active in this realm. By registering tens of thousands of domain names across various registrars, they effectively manage to stay off the radar.
“While security providers may be able to identify and block the final content, without a comprehensive perspective, it becomes challenging to fully comprehend the extent of their operations and link the domains to a single DNS threat actor,” states Infoblox.
Infoblox’s discovery of Prolific Puma began with the implementation of automated analytics, which initially revealed a few interrelated domains. Subsequently, the introduction of algorithms designed for RDGA discovery earlier this year allowed for the identification of domains in clusters. Another algorithm facilitated the correlation of these domain clusters, ultimately attributing them to a single DNS threat actor.
In its report, Infoblox provides a set of indicators for identifying Prolific Puma activity, which includes information such as the IP addresses and domains associated with link shortener hosting, redirection and landing pages, and an email address discovered within domain registration data.
Sources :

